 |
| Selfie, at Rottnest Hotel |
 |
| Perth in the distance, from the front step of Rottnest Hotel |
Some notes:
Smart contracts
From: Blockchain Challenges for Australia: An ACS Technical Whitepaper, by Nick Addison, Samuel Brooks, Katrina Donaghy, Mark Ebeling, Scott Farrell, Vincent Gramoli, Adrian Lawrence, Marc Portlock, Mick Motion-Wise, Bridie Ohlsson, Beth Patterson, Philippa Ryan, Mark Staples, Ingo Weber, and Tom Worthington, 2019, Australian Computer Society, Page 37 (emphasis added). URL http://bit.ly/acsblock“A smart contract can be defined as an event-driven computer program that executes on an electronic distributed, decentralised, shared and replicated ledger used to automate transactions. Even where a smart contract is not technically a ‘contract at law’, it may give rise to obligations and remedies that sound like a contract in law.”
Blockchain Challenges, ACS 2019
Protecting Smart Contracts
From: Fuzzing: The State of the Art, by Richard McNally, Ken Yiu, Duncan Grove and Damien Gerhardy, Command, Control, Communications and Intelligence Division, Defence Science and Technology Organisation, DSTO–TN–1043. URL https://apps.dtic.mil/dtic/tr/fulltext/u2/a558209.pdf“Fuzzing is an approach to software testing where the system being tested is bombarded with test cases generated by another program. The system is then monitored for any flaws exposed by the processing of this input.”
ANU Cyber Reading Group
The Human-Factor in Security
 |
Webpage, SMH, 2013 |
- Social engineering can be used to fool staff to give access to a secure system.
- The attacker collects information used for phishing attacks.
Fake childcare website from: Page, F., & Jean, P. (2013, April 16). Free childcare scam aimed at intelligence staff. Sydney Morning Herald. Retrieved from: http://www.smh.com.au/it-pro/security-it/free-childcare-scam-aimed-at-intelligence-staff-20130415-2hwhq.html
Asia Pacific Hypothetical
"At 02:20 Zulu, 1 April 2017, one of our maritime surveillance aircraft was reported missing. The aircraft was conducting a freedom of navigation flyover on one of the reefs, subject to claim by several nations. The last recorded radio transcript … “Mayday, Mayday, Mayday, this is Surveillance One Zero Five Charlie Delta, one zero zero kilometers South East of ... " [Transmission ends]” ...
RAAF P-3 Orion Aircraft,
photo by 'Timothy'
CC BY 2.0, via Wikimedia Commons
It is proposed to target the opposing force's electronic control systems. This is expected to disable electrical systems and cause some local electrical fires. Our intelligence assets in the area will arrange for video of the damage to be posted to social media, for maximum news value. We will be working with civilian government personnel with special expertise, to prepare a human factor attack on their Internet of Things (IoT)."
From Cyberwar: Hypothetical for Teaching ICT Ethics, by Tom Worthington for the course ANU Networked Information Systems, http://www.tomw.net.au/basic_ict_professional_ethics/#ch170077
Cyberweapons
"the purpose of a cyberweapon is to attack an information system in order to perpetrate harm".
Information Warfare Division (IWD),
Australian Department of Defence
From Henschke, A. (2014). A decision-making procedure for responding to cyber-attacks. In M. Keelty, A. Henschke, N. Evans, S. Ford; A Gastineau; L. West, Cybersecurity: mapping the ethical terrain. National Security College (ANU). URL http://nsc.anu.edu.au/documents/ocassional-paper-6-cyber-ethics.pdf
“Offensive Cyber Security operations introduces and exercises a complete range of reverse engineering techniques and attack patterns. Students will also learn and exercise analysis of systems based on minimal information.”
From ANU (2019). Cyber Offensive Operations Course (COMP8502), ANU Handbook. URL https://programsandcourses.anu.edu.au/2019/course/COMP8502
Reponse to Attack
“Credential theft. … four spearphishing emails, to ANU users ...
Compromised infrastructure. The actor built a shadow ecosystem of compromised ANU machines, tools and network connections to carry out their activities undetected. Some compromised machines provide a foothold into the network. Others, like the so-called attack stations, provided the actor with a base of operations to map the network, identify targets of interest, run tools and compromise other machines
Data theft. The actor used a variety of methods to extract stolen data or credentials from the ANU network. This was either via email or through other compromised Internet-facing machines. …”
From: From Incident Report on the Breech of the Australian National University's Administrative Systems, ANU, 2 October, 2019 URL https://imagedepot.anu.edu.au/scapa/Website/SCAPA190209_Public_report_web_2.pdf
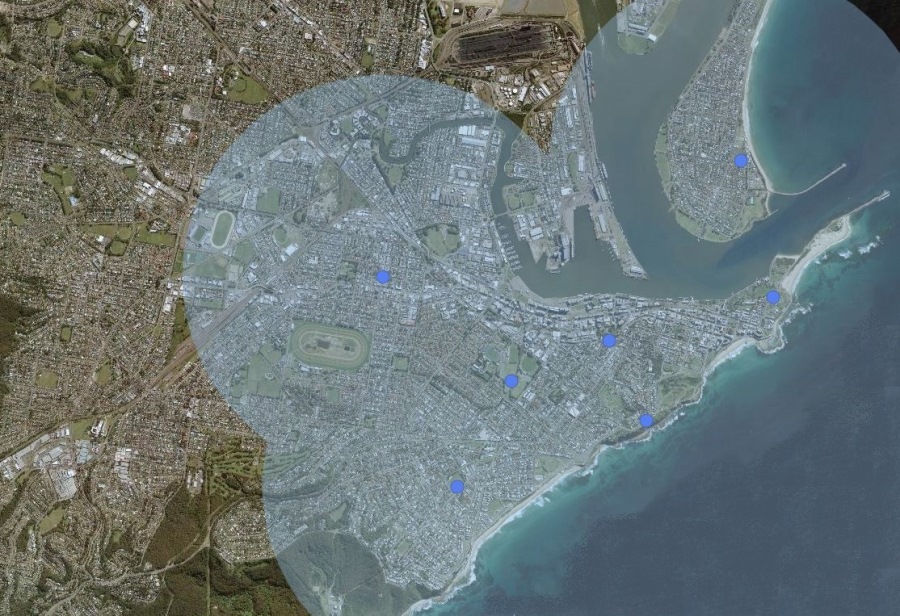
Internet of Things
“The Internet of Things is the interconnection via the Internet of computing devices embedded in everyday objects, enabling them to send and receive data.”
Newcastle IoT Coverage,
City of Newcastle 2018
From: From: Council begins roll out of smart city tech, City of Newcastle, 24 Apr 2018. URL https://www.newcastle.nsw.gov.au/Council/News/Latest-News/Council-begins-roll-out-of-smart-city-tech
ps: ANU to run 'cyber bootcamp' for ASEAN officials, By Matt Johnston
IT News, Nov 11 2019



_-_Logo.png/330px-Information_Warfare_Division_(Australian_Department_of_Defence)_-_Logo.png)
1 comment:
Herbert Smith Freehills have announced their Digital Law Group. I was delighted to be invited to talk to the team about smart contracts, cyber security, IoT, and all things digital, last week.
Post a Comment